Table of Contents
Data Access Management Guide: Implementation + Tools 2026
Regulating access to data is one of the most important aspects of data governance. As a result, data access management has evolved into an independent initiative that requires an autonomous strategy, budget, and implementation schedule.
Data access management, or data access governance, may be the most significant outcome of a data governance initiative. Why? It covers multiple critical areas:
- Maintaining data security
- Protecting PII
- Providing access to critical data assets
- Managing permissions
- Ensuring compliance
According to CrowdStrike, identity-based attack methods are used in 80% of cyberattacks. In 2026, with 91% of organizations acknowledging the need for better AI data governance and identity management, proper data access management has become more critical than ever.
Read on to learn what data access management is, why it's important, how to implement it, and the best practices for developing and maintaining a data access management solution in your organization.
Download the OvalEdge Access Matrix here to keep track of access policies in your organization.
What does Data Access Management mean?
Data access management is a process undertaken by organizations that determines who has access to which data assets. It enables companies to secure confidential information, define ownership of data, and implement managed access controls that enable users to achieve data-driven innovation.
The process governs who can access what data, when they can access it, and how they can access it. It also lays out the models, methods, and technologies required to achieve this result.
Without well-managed access, users can't retrieve the information they require, collaborating on data assets is virtually impossible, data owners don't take responsibility for the data in their care and the risk of non-compliance is high.
In terms of data governance, data access management is crucial. Without well-managed access, users can't retrieve the information they require. Collaborating on data assets becomes virtually impossible. Data owners don't take responsibility for the data in their care. And the risk of non-compliance is high.
Industry research shows that organizations with poor access management experience 3x more data breaches than those with strong controls, and data breaches cost organizations an average of $4.45 million, according to IBM's Cost of Data Breach Report.
Understanding Access Control Models
Before implementing data access management, you need to understand the different access control approaches. Choosing the right model for your organization is critical to balancing security with usability.
Role-Based Access Control (RBAC)
RBAC grants access based on a user's job role within the organization. For example, all users with the "Financial Analyst" role automatically get access to financial data.
Best for: Organizations with clearly defined job roles and moderate security requirements
Pros: Easy to manage, scales well, simple to understand
Cons: Can lead to over-permissioning, less flexible for dynamic needs
Attribute-Based Access Control (ABAC)
ABAC grants access based on multiple attributes, including role, department, location, time of day, and device. For example: "Allow access to HR data if user is in HR department AND accessing from office network AND during business hours."
Best for: Highly regulated industries (healthcare, finance) requiring granular control
Pros: Very flexible, context-aware, precise control
Cons: More complex to configure and maintain
Hybrid Approach
Most modern enterprises use a hybrid approach combining RBAC for baseline permissions with ABAC for sensitive data requiring contextual controls. This provides both simplicity and security where it matters most.
Organizations using automated access provisioning with these models reduce access request turnaround time by 70% compared to manual processes.
Why access management is a crucial part of your overall data strategy
The best way to explain the importance of data access management is through a real-world example.
Real-World Scenario: Healthcare Analytics Project Delayed
A healthcare technology company wanted to build a patient readmission prediction model for a 500-bed hospital system. The project had $2M revenue potential and a 6-month timeline.
The challenge: The analytics team needed access to:
- Electronic health records (EHR) with patient demographics
- Claims data from billing systems
- Clinical notes from multiple departments
Without proper data access management:
- Each department had its own approval process
- IT required separate security reviews for each data source
- Compliance team manually reviewed HIPAA requirements
- No clear data ownership or access request workflow
Result: It took 3 months just to get data access approved. By the time scrubbed data was available, the project timeline had doubled, and margins were severely impacted.
With OvalEdge's data access management:
- Automated access request workflows
- Pre-configured HIPAA-compliant access policies
- Clear data ownership and stewardship
- Access granted in 2 weeks instead of 3 months
The hospital system later implemented OvalEdge and reduced average access request time from 12 weeks to 2 weeks - an 83% improvement.
Many people might perceive data governance as primarily a means to support data access management. It isn't, but although there are numerous other areas of data governance, data access management is one of the most important.
When users manage data access correctly, they are provided with the tools and knowledge to find the data they need to work more efficiently. A tool could take the form of a data governance platform. At the same time, users distribute knowledge via policies that govern how business users should access data.
Related: Data Observability - What it is and Why it is important for your Business
Good data access management ensures data is available across departments and even with external entities, too. For modern businesses, the key to growth in data-driven innovation is collaboration.
Data access management is also crucial for defining data ownership. Once teams identify data owners, they must establish specific rules that govern how the data they are responsible for is managed and maintained. Fail to do this, and there's a risk that companies could lose data.
Most importantly, data access management enables business owners to safeguard PII and other confidential or sensitive data. It achieves this by only allowing verified users access to specific data sets.
When these measures are not in place, there is a real risk of exposing data, and companies could face huge penalties for non-compliance under regulations like GDPR and HIPAA.
Challenges faced by organizations to do data access management
Research shows that 76% of organizations have reported a surge in insider threat activity over the past five years. Additionally, 39% of employees resist access management changes due to a lack of understanding about why changes are happening.
Common challenges include:
No Clear Data Ownership: In many cases, users' department heads can't grant them access to departmental data. This scenario exists because no one can identify who is responsible for the data, and both automation and workflows are nonexistent.
IT Bottlenecks: Instead, users need to go through the IT teams. There is often a huge backlog, and users must wait weeks or even months for a response.
Lack of Structured Workflows: When there are no workflows in place, there is no structure. Even if your manager can confirm your identity and that access is required, you still need someone to grant access to PII if the data you request contains it. There is no automation, something a data governance tool like OvalEdge can provide.
Over-Permissioning: Without regular reviews, users accumulate access they no longer need. Studies show 70% of employees retain access to systems they no longer require for their jobs.
Shadow IT and Unmanaged Systems: Users create their own data repositories outside IT control, creating security blind spots.
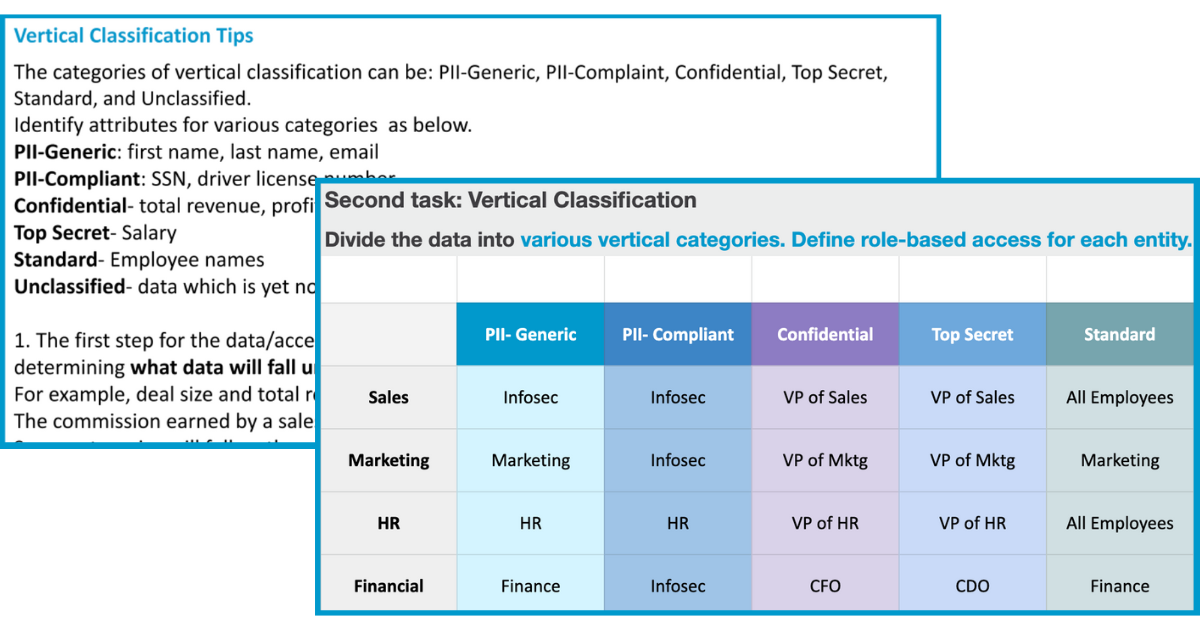
When clearly defined policies are in place, it's easy to determine who a user is and what access permissions they should have. For example:
- Everyone can access public data
- PII data needs information security approval
- Confidential data needs HR approval
This ease of access is a core reason why identifying data owners is so important. It enables business users, even data stewards, to grant access to information independently from IT.
Steps to implement successful data access management
There are a series of critical steps to implementing a data access management initiative. We’ve laid them out here in order.
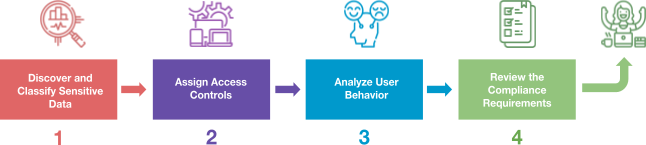
1. Discover and Classify Sensitive Data
The first step in a data access management strategy is to identify where all of your data is stored. Once you discover it, you need to take further steps to tag and classify it in relation to its sensitivity.
Action steps:
- Use automated data discovery tools to scan all repositories
- Tag data by sensitivity: Public, Internal, Confidential, Restricted
- Identify PII, PHI, financial data, and trade secrets
- Document data locations, formats, and volumes
When data is correctly classified, you can focus on securing your most sensitive data assets. This will enable you to pinpoint resources and efforts more efficiently.
Once you know where all your data is stored and what it is, you can delete any redundant data assets. The final step in this initial process is to conduct a risk assessment.
Estimated time: 2-4 weeks for comprehensive data discovery
2. Assign Access Controls
Utilizing the risk assessment you completed in the first stage, you can create access controls for individual business users. However, instead of granting access on a user-by-user basis, it's better to allocate permissions based on defined roles, responsibilities, and data classification.
When clearly defined policies are in place, it's easy to determine who a user is, and the access permissions.
This approach is far easier to administer and requires less of an investment. Access groups will likely be split into categories such as administrators or managers. The key is not to grant access to any user unless they expressly need it.
Access policies based on classifications can be framed in a data governance committee meeting based on classification groups in a robust access policy framework. Download the OvalEdge Access Matrix here to keep track of access policies in your organization.
3. Analyze User Behavior
The next step is to establish a series of analysis techniques to monitor user behavior. This analysis should be an ongoing process.
The aim is to analyze how business users change, duplicate, create, or remove sensitive data from your company's systems. This analysis will enable you to determine whether the user had the authority to make the modifications they did and whether any changes need to be reversed.
Action steps:
- Implement access logging for all sensitive data
- Set up real-time alerts for suspicious activity
- Use user behavior analytics (UBA) to detect anomalies
- Create audit trails for compliance purposes
- Review access logs regularly
When you commit to continuous monitoring of your users, you can quickly identify and act on any potential threats to the security of your data. Organizations with proper monitoring prevent 60% of over-permissioning issues through regular reviews.
Ongoing process with quarterly formal reviews recommended
4. Review Compliance Requirements
Compliance is a key outcome of successful data governance. And, as we mentioned earlier in this article, it is directly related to data access management. The first thing you need to do is identify which regulations are applicable to your organization.
Key compliance frameworks requiring access controls:
- GDPR: Article 32 requires "appropriate technical and organizational measures" for data security
- HIPAA: Security Rule mandates access controls for Protected Health Information (PHI)
- SOC 2: Requires documented access policies, regular reviews, and audit trails
- PCI DSS: Strict access controls for payment card data
By the time you complete all of the steps we outline above, it's unlikely that you will violate any compliance regulations. However, for many regulatory bodies, you'll still need to prove this by completing a compliance certificate and maintaining documentation.
Action steps:
- Map your access controls to regulatory requirements
- Document compliance evidence
- Schedule regular compliance audits
- Update policies based on new regulations
Estimated time: 1-2 weeks for initial compliance mapping, ongoing reviews quarterly
Data Access Management Trends in 2026
The landscape of data access management continues to evolve rapidly. Here are the key trends shaping the field in 2026:
AI and GenAI Governance: Organizations face new challenges in managing access to AI training data and preventing sensitive data leakage into large language models. 91% of organizations acknowledge the need to enhance transparency about how AI handles their data.
Zero Trust Architecture: The "never trust, always verify" security model has become standard for data access management in 2026. Continuous authentication and validation are now expected, not exceptional.
Automated Access Intelligence: AI-powered tools now automatically suggest appropriate access levels based on role, usage patterns, and risk scores, reducing manual provisioning time by 70%.
Cloud-First Access Management: With 85% of enterprises using multi-cloud strategies, unified access policies across cloud providers (AWS, Azure, GCP) are now essential.
Privacy-Enhancing Technologies (PETs): Data masking, tokenization, and homomorphic encryption allow users to work with data while maintaining privacy compliance.
Best practices for data access management
Organizations using these best practices achieve 83% fewer security incidents related to data access:
- Conduct Regular Access Reviews
Schedule quarterly access reviews to verify users still need their current permissions. Remove access immediately when employees change roles or leave the organization.
How to implement:
- Create automated review reminders every 90 days
- Require data owners to certify user access
- Use access analytics to flag unused permissions
- Document review findings for compliance audits
- Create an Inventory
You must create an inventory of everyone who has access to data in your organization. This will enable you to keep track of data usage and record any changes to data access.
- Identify Data Ownership and Location
A fundamental part of good data access management is to identify where your data is stored and who is responsible for it. When you don't identify data owners, data can be mistreated or even lost.
You should also have a system of rewards in place for data ownership responsibilities to incentivize data owners.
- Apply the Principle of Least Privilege
Grant users the minimum access required to perform their job functions. Start with no access and add permissions only as needed, rather than giving broad access and restricting later.
- Implement Multi-Factor Authentication (MFA)
Require at least two verification factors for accessing sensitive data: something you know (password), something you have (phone/token), or something you are (biometric). MFA blocks 99.9% of automated attacks.
- Create a Security Group
One of the best ways to maintain data access security in your organization is to create a series of security groups. These groups can oversee data access and must include representatives from each company department that deals with data. Consider establishing a formal data governance committee structure.
- Conduct Regular Audits
Unless you regularly audit the activities of data users and owners, you won't be able to track the success of your strategy. Schedule audits quarterly at a minimum.
- Create a Certification Program
If you install an access certification program, you can ensure that your users are working with data correctly and with a desired degree of literacy. Provide ongoing data literacy training to all users.
- Automate Where Possible
Manual access management doesn't scale. Use automated workflows for access requests, provisioning, and de-provisioning to reduce turnaround time from weeks to days.
A full-fledged data governance tool adds convenience
Data access management is far more effective and less labor-intensive when companies use a data governance tool to aid them. A data governance platform like OvalEdge enables users to streamline the implementation process.
For example, when it comes to assigning user controls, this process can be automated, so that users are blocked from accessing content that they aren't permitted to view.
In another example, a data governance tool makes it effortlessly simple to find data sources and catalog them in a single location using automated data discovery.
OvalEdge provides:
- Automated access request workflows with approval routing
- Policy-based access controls aligned with data classification
- Integration with IAM systems for seamless authentication
- Real-time monitoring and audit trails
- Compliance reporting for GDPR, HIPAA, SOC 2
Organizations using OvalEdge report 70% faster access provisioning and 83% reduction in access-related security incidents.
FAQs
What is data access management in simple terms?
Data access management is the process of controlling who can access, view, and modify your organization's data assets. It determines which users have permission to specific data, when they can access it, and what actions they can perform. This ensures both security and compliance while enabling authorized users to work efficiently.
What is the difference between data access management and identity management?
Identity and Access Management (IAM) focuses on user identities and authentication - proving who you are (username, password, MFA). Data access management focuses on authorization - what data those authenticated users can access. IAM answers "who are you?" while data access management answers "what can you access?" Both work together in a complete security framework.
What are the main types of access control models?
There are three primary access control models:
Role-Based Access Control (RBAC): Access granted based on job role (e.g., all Financial Analysts access financial data). Best for organizations with clear role definitions.
Attribute-Based Access Control (ABAC): Access based on multiple attributes like role + department + location + time. Best for highly regulated industries requiring granular control.
Mandatory Access Control (MAC): Access based on data classification levels (Public, Confidential, Restricted). Used in government and high-security environments.
Most modern enterprises use a hybrid approach combining RBAC for simplicity with ABAC for sensitive data.
Why is data access management important for compliance?
Data access management is required by virtually every major compliance framework. GDPR Article 32 mandates "appropriate technical measures" for data security. HIPAA's Security Rule requires access controls for Protected Health Information. SOC 2 demands documented access policies and regular reviews. Without proper access management, organizations face significant fines (up to 4% of global revenue for GDPR violations) and cannot pass compliance audits.
How long does it take to implement data access management?
Timeline varies by organization size and complexity:
- Basic framework: 2-3 months for small organizations (<500 employees)
- Comprehensive deployment: 4-6 months for medium organizations (500-2,000)
- Enterprise-wide implementation: 6-12 months for large organizations (2,000+)
Using a platform like OvalEdge can reduce implementation time by 50-70% through automation and pre-built policy templates.
What tools are needed for data access management?
A complete data access management solution typically includes:
- Identity and Access Management (IAM): User authentication (Okta, Azure AD, AWS IAM)
- Data Catalog: Discovery and classification (OvalEdge, Collibra, Alation)
- Access Control Enforcement: Database and application-level controls
- Monitoring and Auditing: Access logging and anomaly detection (Splunk, Varonis)
- Data Masking: Protect sensitive fields for unauthorized users
OvalEdge provides a unified platform combining data catalog, access workflows, and policy management, eliminating the need for multiple point solutions.
What are common data access management challenges?
The most common challenges organizations face:
- No clear data ownership - Nobody knows who's responsible for granting access
- IT bottlenecks - Access requests take weeks or months through IT
- Over-permissioning - 70% of employees retain access they no longer need
- Shadow IT - Unmanaged data repositories outside IT control
- Legacy systems - Old systems don't support modern access controls
- User resistance - 39% of employees resist changes they don't understand
Proper planning and stakeholder engagement help overcome these challenges.
How often should access permissions be reviewed?
Best practice timeline:
- Quarterly reviews: For access to sensitive data (PII, financial, PHI)
- Immediate reviews: When employees change roles or leave
- Annual reviews: For access to general internal data
Automated access certification tools can reduce review time by 60% while improving accuracy. Organizations that conduct quarterly reviews prevent 60% of over-permissioning issues.
What is the difference between data access management and data governance?
Data access management is a subset of broader data governance. Data governance encompasses policies, standards, and processes for all aspects of data management, including quality, metadata, lineage, privacy, and access. Data access management specifically focuses on controlling who can access what data. Think of data governance as the overall strategy, and data access management as one critical component of that strategy.
How can I measure data access management success?
Track these key metrics:
Efficiency Metrics:
- Access request turnaround time (target: <3 days)
- Percentage of requests automated vs. manual
- Time spent by IT on access management
Security Metrics:
- Number of unauthorized access attempts
- Access-related policy violations
- Failed audit findings
Compliance Metrics:
- Percentage of users reviewed in last quarter
- Time to revoke access for terminated employees
- Compliance audit pass rate
Business Value:
- Reduction in data breach risk
- Time saved by business users finding data
- Revenue impact from faster data access
Organizations with mature data access management see 70% faster access provisioning, 83% fewer security incidents, and 100% compliance audit success rates.
Conclusion
Without a sufficient data access management strategy, your data governance initiative will fail. Data access is more than just protecting sensitive data. Without access management in place, you can't expect your users to derive the potential value from the data at their disposal.
In 2026, with 80% of cyberattacks using identity-based methods and average breach costs exceeding $4.45 million, proper data access management is not optional - it's essential for business survival and growth.
However, you can't dive straight in with a data management initiative. Just like a full-fledged data governance plan, it has to be measured and carried out methodically.
Book a call with us to find out:
|
Deep-dive whitepapers on modern data governance and agentic analytics
OvalEdge recognized as a leader in data governance solutions
.png?width=1081&height=173&name=Forrester%201%20(1).png)
“Reference customers have repeatedly mentioned the great customer service they receive along with the support for their custom requirements, facilitating time to value. OvalEdge fits well with organizations prioritizing business user empowerment within their data governance strategy.”
.png?width=1081&height=241&name=KC%20-%20Logo%201%20(1).png)
“Reference customers have repeatedly mentioned the great customer service they receive along with the support for their custom requirements, facilitating time to value. OvalEdge fits well with organizations prioritizing business user empowerment within their data governance strategy.”
Gartner, Magic Quadrant for Data and Analytics Governance Platforms, January 2025
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
GARTNER and MAGIC QUADRANT are registered trademarks of Gartner, Inc. and/or its affiliates in the U.S. and internationally and are used herein with permission. All rights reserved.



