Table of Contents

Data Security in Snowflake: How OvalEdge Enables Secure Data Sharing & Governance
OvalEdge has completed the Snowflake Ready Validation Program. This third-party technical validation process confirms that OvalEdge integration is optimized for Snowflake functionality and aligned with best practices for Data Security in Snowflake.
The focus of the validation was to provide Snowflake customers with secure, managed, universal access to assets in their data lake and support secure data sharing in Snowflake without creating new risks.
What's the Data Security Challenge in Snowflake?
Generally, in managed systems like SAP and Oracle Apps, a complete security system is in place that determines who can access which data.
For example, a member of the HR team might only have access to salary data, a member of the Procurement team may be limited to accessing purchasing information, and a Sales Representative sales information.
Once this data is moved over to a data lake built in Snowflake, it is tough to provide universal access, as there are no security rules in place.
Although Snowflake has all the features in place to secure access to data, determining who is provided what access is a challenge, as there could be millions of attributes to consider.
Related: How End-to-End Data Governance in Snowflake Supports Business Agility
How OvalEdge tackles security challenges in Snowflake
Four pillars of secure data access
The four areas of data security the OvalEdge platform addresses in Snowflake are classification, roles and responsibilities, data protection, and monitoring. Together, they create a complete strategy for Data Security in Snowflake and govern secure data sharing in Snowflake.
Classify → Define Roles and Responsibilities → Protect → Monitor
Classification
Data classification is the critical first step for enforcing role-based access and is the cornerstone of Data Security in Snowflake. First, you will divide your data horizontally.
This is relatively easy as horizontal classifications are based on various business functions, such as Sales, HR, Marketing, and Finance.
With this methodology, the implementation is relatively more straightforward. You must be able to find some common thread to classify your data based on applications, databases, etc.
With horizontal classification, assigning access owners for various categories becomes easy.
The second task is to classify the data vertically. Vertical classification divides the data into categories like PII-Generic, PII-Complaint, Confidential, Top Secret, Standard, and Unidentified.
All data that is not yet classified will come under Unidentified Data. Vertical classification is an intricate process involving these steps:
- The first step is for the data/access owners of the horizontally classified data to make policies determining what data will fall under which category within their department.
- For example, deal size and total revenue within the Sales department could fall under ‘confidential.’ The commission earned by a sales rep on a deal could fall under ‘top secret.’
- Some categories will follow the same conventions across various departments.
PII-Generic: First name, last name, email
PII-Compliant: SSN, driver's license number
- The next step is to define role-based access policies for all the categories of fully classified data.
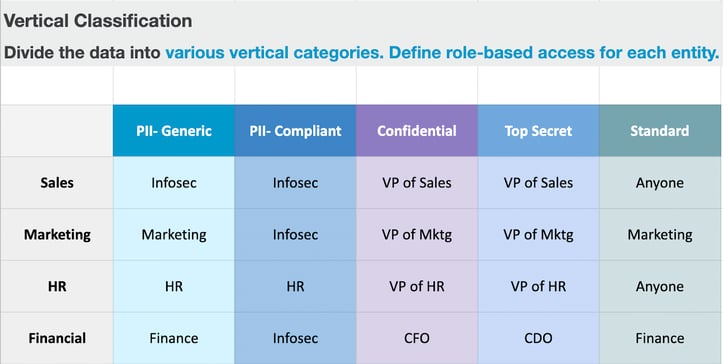
Example Matrix
OvalEdge enables customers to write policies for each classification, use AI to classify the data, and automatically enforce policies as data is classified. OvalEdge syncs these classifications directly with Snowflake to enforce tag-based security automatically, a prerequisite for any secure data sharing in Snowflake.
Roles and Responsibilities
Once organizations have classified their data in OvalEdge, they must design an approval process based on these classifications. The various data governance roles and responsibilities in an organization support access policies.
Data governance roles usually include admin, steward, custodian, and user. These roles carry various responsibilities, and while a user may only have access to limited data sets, an admin will have the power to designate access to others.
Our platform Ovaledge supports two-way syncing of these user roles and permissions with Snowflake, which is essential for managing permissions across the data landscape and for governing secure data sharing in Snowflake.
Protect: Masking and Restricting Sensitive Data
To prevent unauthorized access, a core goal of Data Security in Snowflake sensitive information must be protected. OvalEdge allows you to define policies that automatically mask or restrict data based on a user's role.
This data protection can be applied at the source, before the data even reaches your Snowflake data warehouse, ensuring raw sensitive data is never exposed, whether in internal use cases or in secure data sharing in Snowflake with external parties.
Monitor: Continuous Security Assurance
Data Security in Snowflake is not a one-time event. OvalEdge provides continuous data monitoring. Whenever new data is detected, our AI automatically triggers an approval request to the relevant data owner or steward.
This ensures your data access security measures are consistently maintained, even as your data ecosystem evolves, safeguarding all operations, including dynamic secure data sharing in Snowflake.
FAQs
1. What is Data Security in Snowflake?
Data Security in Snowflake refers to the processes, controls, and governance practices that protect sensitive data stored or shared within Snowflake. This includes access policies, masking, classification, encryption, and monitoring.
2. How does OvalEdge improve secure data sharing in Snowflake?
OvalEdge automates data classification, role-based access, masking, and approval workflows. This ensures only authorized users can view or share sensitive Snowflake data.
3. Why is data classification important in Snowflake?
Without classification, organizations cannot enforce consistent access rules. Classification enables tag-based policies, masking, and compliant data sharing.
4. Can Snowflake handle enterprise-level security on its own?
Snowflake provides strong platform-level controls, but enterprise teams still need external governance tools (like OvalEdge) to define business-aligned policies and determine who should access what.
5. How does OvalEdge sync with Snowflake?
OvalEdge performs two-way syncing of metadata, roles, permissions, classifications, and tags to maintain consistent governance across both platforms.
6. What kind of data can be masked using OvalEdge?
OvalEdge can mask PII, financial data, healthcare data, employee-level data, and any custom classified field.
7. Does OvalEdge support auditing and monitoring?
Yes. OvalEdge automatically sends approval requests and logs all access events, ensuring continuous oversight.
8. Is secure data sharing in Snowflake suitable for large enterprises?
Yes. With proper governance tools like OvalEdge, enterprises can safely scale secure data sharing while maintaining compliance and reducing operational risk.
What you should do now
|
Deep-dive whitepapers on modern data governance and agentic analytics
OvalEdge recognized as a leader in data governance solutions
.png?width=1081&height=173&name=Forrester%201%20(1).png)
“Reference customers have repeatedly mentioned the great customer service they receive along with the support for their custom requirements, facilitating time to value. OvalEdge fits well with organizations prioritizing business user empowerment within their data governance strategy.”
.png?width=1081&height=241&name=KC%20-%20Logo%201%20(1).png)
“Reference customers have repeatedly mentioned the great customer service they receive along with the support for their custom requirements, facilitating time to value. OvalEdge fits well with organizations prioritizing business user empowerment within their data governance strategy.”
Gartner, Magic Quadrant for Data and Analytics Governance Platforms, January 2025
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
GARTNER and MAGIC QUADRANT are registered trademarks of Gartner, Inc. and/or its affiliates in the U.S. and internationally and are used herein with permission. All rights reserved.


