Table of Contents
Master Data Obfuscation in 2026: Essential Methods & Benefits
In today's digital world, data is a valuable asset that businesses rely on for decision-making, operations, and competitive advantage. But with the increasing risk of data breaches and privacy concerns, protecting sensitive information has become a top priority for companies.
One technique that can help safeguard your customers’ information is data obfuscation.
According to recent industry findings, the average cost of a data breach dropped slightly to USD 4.44 million in 2025, but remains at a critical level.
Even more revealing: 60% of all breaches in 2025 involved the human element—errors, misuse of credentials, and social engineering.
These numbers underline how critical proactive security strategies like data obfuscation have become in protecting sensitive information.
But what exactly is data obfuscation, and why is it important to your business? In this blog post we will cover:
- What is data obfuscation?
- Why data obfuscation is important
- Benefits of data obfuscation
- Data obfuscation best practices
Analyze the various aspects of Data Privacy Compliance before revealing how OvalEdge can address them in your company. Download our whitepaper How to Ensure Data Privacy Compliance with OvalEdge
What is data obfuscation?
Data obfuscation is a technique used to protect sensitive or confidential data by disguising it or making it less understandable. This protects the data, while allowing it to be used for other tasks and purposes.
The goal of data obfuscation is to make it impossible for unauthorized users to attribute the data, reducing the risk of unauthorized access or misuse.
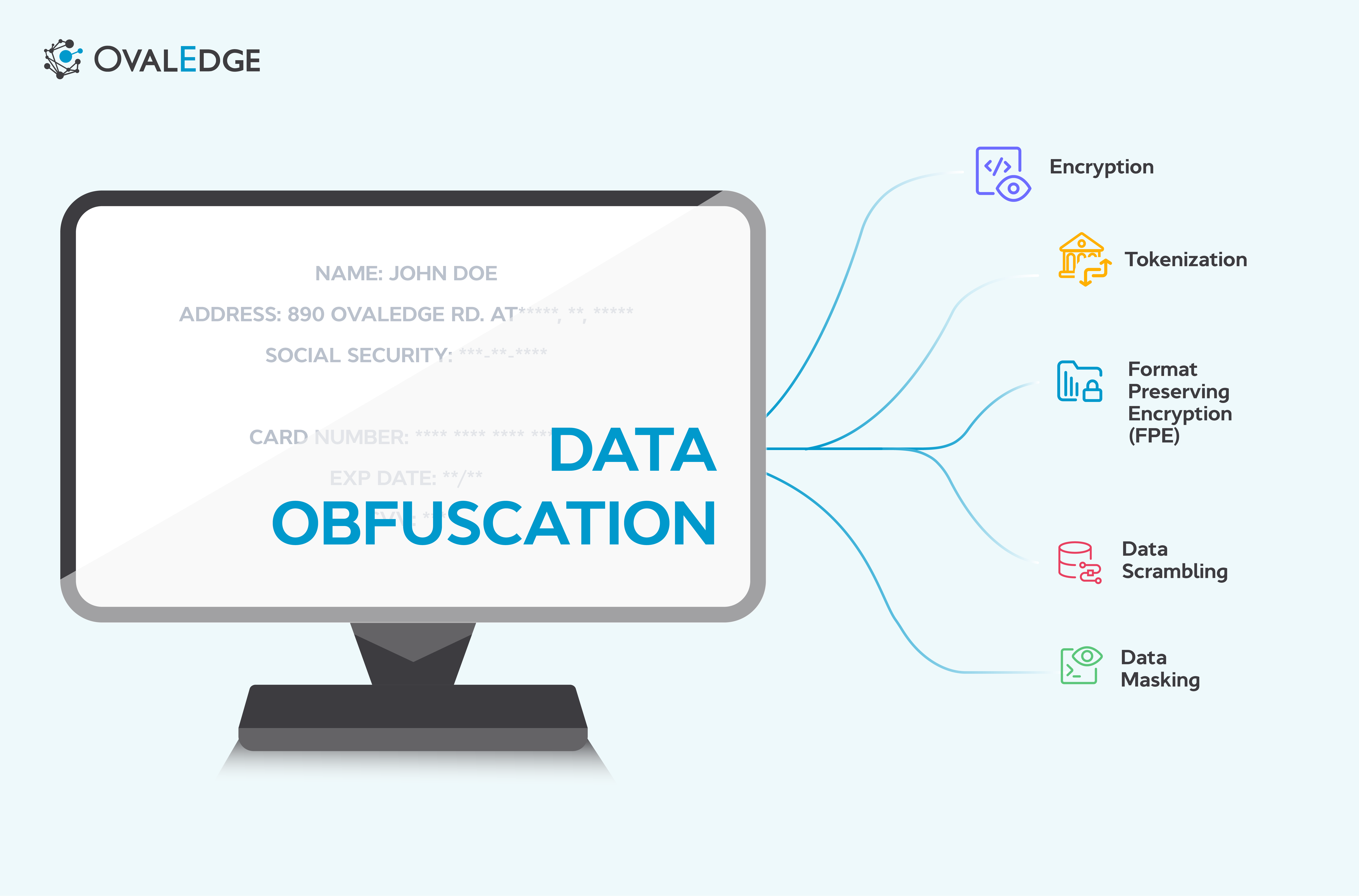
It can take various forms, such as encryption, tokenization, data masking, and data scrambling. We’ll dive into these in more detail later on.
Data obfuscation is typically applied to different types of sensitive data, such as personally identifiable information (PII), financial data, intellectual property, and other confidential information.
It can be implemented during data storage, transmission, or processing, and can be used in various data environments, such as databases, applications, and cloud-based systems.
Data obfuscation is not a one-size-fits-all solution, and the choice of obfuscation technique depends on your specific requirements. But the common goal of data obfuscation is to provide an additional layer of protection to sensitive data, making it harder for unauthorized users to access the data.
In the nexct section, we will delve into why data obfuscation is important to your business, and the benefits it can provide in safeguarding sensitive data and mitigating data-related risks.
Why is data obfuscation important?
Data obfuscation plays a key role in protecting sensitive data and mitigating the risks associated with data breaches and privacy concerns. Here are some key reasons why data obfuscation is important for businesses:
Data Privacy Compliance
Compliance with data privacy regulations, such as the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and other industry-specific regulations, is a legal requirement for businesses.
Data obfuscation helps companies meet these compliance requirements by protecting sensitive data from unauthorized access or unintended disclosure, reducing the risk of regulatory fines, penalties, and legal liabilities.
Related: 3 Data Privacy Compliance Challenges that can be solved with OvalEdge
Data Security
Data breaches can have severe consequences for businesses, including financial losses, reputational damage, and legal liabilities.
Data obfuscation adds an additional layer of security to sensitive data, making it more challenging for unauthorized users to interpret or decipher the data, thereby reducing the risk of data breaches and other security incidents.
Risk Mitigation
Data obfuscation is a proactive risk management tactic that helps businesses identify and mitigate vulnerabilities in their processes, systems, and applications.
By obfuscating sensitive data, businesses reduce the risk of data theft, data misuse, and unintended data exposure. Strengthening their data security posture across the board.
Data Sharing and Outsourcing
Many businesses share data with partners, vendors, or third-party service providers for various purposes. These include analytics, marketing, and operations.
Data obfuscation helps protect shared data from unauthorized access or misuse, ensuring sensitive information remains confidential and secure, even when shared externally.
This can be particularly important when outsourcing data processing or storage to third-party providers.
Customer Trust and Brand Reputation
Data privacy and security are critical concerns for customers, and businesses that prioritize data protection through data obfuscation can build customer trust and enhance their brand reputation.
Demonstrating strong data protection practices can differentiate a business from its competitors and generate customer loyalty and retention.
Competitive Advantage
In today's data-driven business landscape, robust data protection measures, like data obfuscation, can give a business a competitive advantage.
It can be a distinguishing factor that sets a business apart from its competitors and instills confidence in customers and partners.
Challenges & Solutions
-
Balancing data usability with stringent privacy requirements remains a top challenge. Over-obfuscation can degrade data utility, while under-obfuscation risks data exposure.
-
Intelligent automation tools that dynamically adjust obfuscation levels based on use-case contexts are emerging solutions.
-
Compliance with multiple data privacy regulations across jurisdictions demands centralized policy management with real-time enforcement capabilities integrated into obfuscation frameworks.
Techniques for data obfuscation
There are a number of techniques you can use to hide or mask sensitive data in order, and protect it from unauthorized access. Here are some common techniques:
- Encryption: A process of converting data into a code using special formulas. This code can only be decrypted with a specific key, which is known only to authorized users. Encryption is like putting a lock on the data, so only those with the right key can unlock and access it.
- Tokenization: This involves replacing sensitive data with non-sensitive placeholders called tokens. The original data is stored securely, while the tokens are used for legitimate tasks like processing transactions or generating reports. Tokenization is like replacing sensitive data with a fake ID, so that the real information is hidden and protected.
- Data Masking: A technique where you replace sensitive data with fictional or scrambled values, while maintaining the data's format and structure. This can be done by randomizing, substituting, or shuffling data values. Data masking is like disguising the original data with a fake mask, so that the real data remains hidden.
- Data Scrambling: Where you shuffle or reorder data elements to create a new version of the data that is not recognizable. This can be done by changing the order of information using different algorithms. Data scrambling is like rearranging the pieces of a puzzle, so that the original data becomes difficult to decipher.
- Format Preserving Encryption (FPE): FPE is a specialized form of encryption that maintains the format and structure of the original data while encrypting it. This allows businesses to encrypt sensitive data without changing the format or length of the data. This makes it suitable for applications that require the data to maintain its original format.
- AI-Powered Obfuscation: With the advancement of artificial intelligence, new obfuscation methods leveraging machine learning algorithms dynamically adapt masking levels according to detected threat intensities, improving data utility without compromising privacy.
- Latent Space Projection (LSP): An innovative approach transforming data points into dense vector spaces that mask original values while preserving analytical utility, perfect for privacy-preserving data sharing and AI model training.
As well as these techniques, there are also various data obfuscation tools available that offer automated and customizable data obfuscation techniques. These tools provide businesses with options to choose from different obfuscation methods and apply obfuscation at various levels, making it convenient and efficient to implement data obfuscation measures.
Related: Data Observability: What it is and Why it is important for your Business
Key Benefits of Data Obfuscation
Beyond compliance, data obfuscation is becoming essential to maintain resilience. Studies show that 53% of all breaches involve customer PII, while the mean time to identify and contain a breach averaged 241 days in 2025 — a nine-year low but still too long.
Best practices for data obfuscation
Implementing data obfuscation in a business environment requires careful planning and execution to ensure that sensitive data is effectively protected. There are a number of best practices you can follow, which will help you achieve this:
1. Identify and Classify Sensitive Data
Begin by identifying and classifying the sensitive data that needs to be protected. This includes personally identifiable information (PII), financial information, intellectual property, trade secrets, etc. This includes any data that could potentially cause harm if unauthorized users access it.
2. Understand Data Privacy Regulations
Familiarize yourself with relevant data privacy regulations, such as GDPR, HIPAA, or CCPA, that apply to your business. These regulations provide guidelines and requirements for protecting sensitive data, and compliance with these regulations is crucial for avoiding legal and financial penalties.
3. Choose Appropriate Obfuscation Techniques
Select the appropriate obfuscation techniques based on the type of sensitive data, the intended use of the data, and the level of protection required. Consider factors such as the effectiveness of the obfuscation technique, the impact on data usability, and the effort required for implementation.
4. Use Multiple Obfuscation Layers & Keep Keys Secure
Employ multiple layers of obfuscation to add an extra layer of security. For example, tokenization, encryption and data masking can be used to create a multi-layered approach that makes it more difficult for unauthorized users to decipher your data.
It’s also vital to safeguard the obfuscation keys used in encryption or tokenization to prevent unauthorized access. Use secure key management practices, such as encryption and access controls, to protect the keys from unauthorized access or disclosure.
5. Test and Validate Obfuscated Data
Verify the effectiveness of the data obfuscation techniques by testing and validating the obfuscated data. This can involve penetration testing, vulnerability assessments, or other security testing methods to identify potential weaknesses or vulnerabilities in the obfuscated data.
6. Regularly Review and Update Obfuscation Measures
Data obfuscation isn’t a one-and-done process. Regularly review and update your obfuscation measures to keep up with changing security requirements, evolving threats, and updates to data privacy regulations.
Start with data classification. The data-classification market alone is projected to reach USD 924.3 million by 2026, reflecting the surge in organisations prioritising data discovery before applying obfuscation layers.
Market Trends & Adoption
- The global data obfuscation market is expanding rapidly and is expected to reach USD 5.8 billion by 2033, growing at a CAGR of 16.9%. This surge is due to increasing regulatory pressures such as GDPR and HIPAA and the rise of sophisticated cyber threats necessitating robust data protection methods.
- Key industries implementing data obfuscation extensively include banking, healthcare, and retail, aiming to comply with regulations and mitigate risks related to data breaches.
Best Practices to Strengthen Data Obfuscation
- Implementing policy-driven obfuscation ensures automated and consistent application of masking, tokenization, or encryption based on data sensitivity classification, which enhances compliance effectiveness and reduces human errors.
- Utilizing multi-layered obfuscation, combining methods like tokenization and encryption, further complicates unauthorized deciphering attempts. Critical too is secure key management practices, employing encryption and strict access controls to safeguard keys.
- Routine testing and validation of obfuscated data, involving penetration testing and vulnerability assessments, help ensure ongoing robustness of obfuscation measures against emerging threats.
Conclusion
Implementing data obfuscation in a business environment is essential for protecting sensitive data. And by following the best practices we outlined, your businesses can effectively safeguard sensitive data and maintain regulatory compliance.
Data obfuscation should be considered an integral part of a comprehensive data security strategy, not just a one-time process. It requires ongoing effort to keep up with changing security requirements, evolving threats, and updates to data privacy regulations.
By prioritizing data obfuscation, you can ensure your sensitive data remains protected, reducing the risk of data breaches and privacy violations.
Safeguarding sensitive data is not only important for protecting the reputation and financial stability of a business, but also for maintaining the trust and confidence of customers and stakeholders.
FAQs
Q1. What are some popular data obfuscation tools in 2025?
A: Leading tools include Delphix, Broadcom, IBM InfoSphere Optim, Immuta, and Microsoft Azure Data Masking. Several open-source options exist for flexible development use.
Q2. How do data masking and obfuscation differ?
A: Data masking replaces real data with fictitious but structurally similar data, while obfuscation broadly includes encryption, tokenization, and scrambling to make data unreadable.
Q3. What are common data obfuscation methods?
A: Common methods include encryption, tokenization, data masking, data scrambling, and format preserving encryption.
Q4. Are there open-source data obfuscation tools available?
A: Yes, open-source options like Apache Ranger and community data masking libraries on GitHub offer cost-effective solutions with customizable capabilities.
Q5. Why should businesses invest in data obfuscation tools?
A: These tools automate data protection, ensure compliance with privacy laws like GDPR and HIPAA, reduce risk of breaches, and maintain data utility for analytics and operations.
What you should do now
|
Deep-dive whitepapers on modern data governance and agentic analytics
OvalEdge recognized as a leader in data governance solutions
.png?width=1081&height=173&name=Forrester%201%20(1).png)
“Reference customers have repeatedly mentioned the great customer service they receive along with the support for their custom requirements, facilitating time to value. OvalEdge fits well with organizations prioritizing business user empowerment within their data governance strategy.”
.png?width=1081&height=241&name=KC%20-%20Logo%201%20(1).png)
“Reference customers have repeatedly mentioned the great customer service they receive along with the support for their custom requirements, facilitating time to value. OvalEdge fits well with organizations prioritizing business user empowerment within their data governance strategy.”
Gartner, Magic Quadrant for Data and Analytics Governance Platforms, January 2025
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
GARTNER and MAGIC QUADRANT are registered trademarks of Gartner, Inc. and/or its affiliates in the U.S. and internationally and are used herein with permission. All rights reserved.