Table of Contents
5 Pillars of Data Privacy Compliance for Organizations
Many organizations handle personal data daily but struggle to translate privacy laws into consistent, operational practices. Compliance efforts often become fragmented or reactive, creating gaps that surface during audits, complaints, or data breaches. The five pillars of data privacy compliance offer a clear framework that regulators use to assess accountability, risk management, documentation, and incident response. Together, they define how privacy responsibilities are assigned, risks are managed, and controls are sustained across the organization.
Privacy compliance often becomes urgent only when something goes wrong. A regulator asks for documentation that no one can find. A vendor rollout triggers questions about consent and risk that were never assessed. A breach exposes gaps that leadership assumed were already covered. Many organizations in the Philippines find themselves in this situation, not because they ignore privacy, but because their compliance efforts are scattered across policies, spreadsheets, emails, and disconnected teams.
This fragmentation is risky at a time when enforcement is tightening. According to McKinsey, organizations that fail to operationalize data privacy and trust lose customer confidence faster and face significantly higher regulatory and remediation costs when incidents occur.
That is where a pillar-based approach becomes essential. Instead of treating compliance as a checklist or a security-only problem, the five pillars of data privacy compliance provide a practical framework to organize responsibilities, reduce blind spots, and sustain compliance over time.
This guide breaks down those five legally grounded pillars and shows how they work together to build a defensible, audit-ready privacy program.
What are the 5 pillars of data privacy compliance?
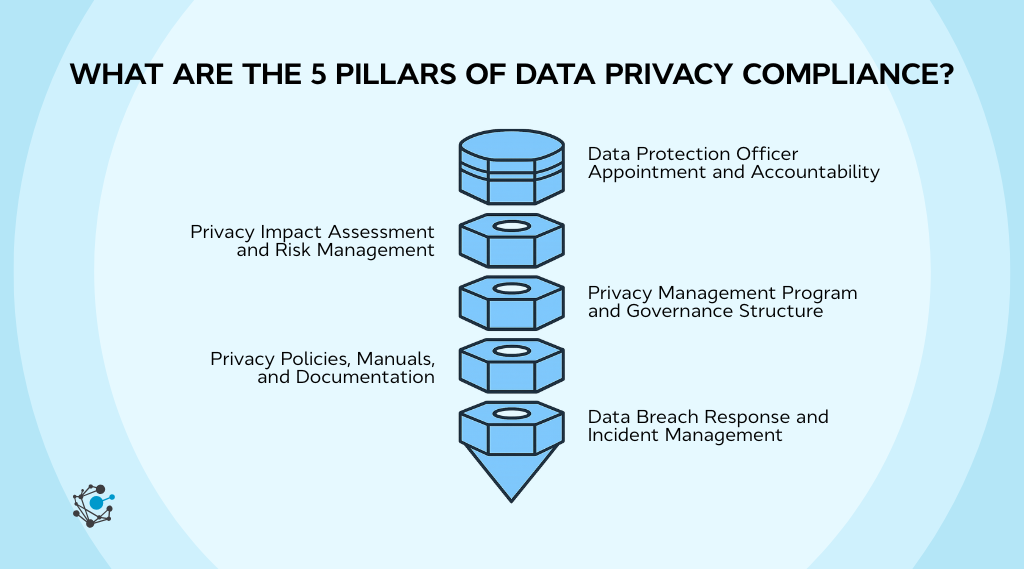
The five pillars of data privacy compliance are the core components that regulators expect organizations to establish, document, and sustain to demonstrate accountability under the Philippines Data Privacy Act of 2012 and similar privacy laws globally. Together, they form a complete privacy compliance framework that goes beyond security controls and addresses governance, risk, and response.
In practice, this framework is built on five interconnected pillars that define how privacy responsibility is assigned, risks are evaluated, controls are documented, and incidents are managed across the organization.
-
Data Protection Officer (DPO) appointment and accountability
This pillar establishes clear ownership for privacy compliance. It covers when a DPO is legally required, how accountability is assigned, and how organizations demonstrate responsibility through proper designation, registration, and ongoing oversight. -
Privacy Impact Assessment (PIA) and risk management
This pillar focuses on identifying and mitigating risks to data subjects before harm occurs. It ensures high-risk processing activities are assessed, documented, and approved, rather than addressed reactively after issues arise. -
Privacy Management Program and governance structure
This pillar defines how privacy is operationalized across the organization. It covers governance frameworks, role clarity, escalation paths, and mechanisms that embed privacy into day-to-day business operations instead of isolating it within legal or IT teams. -
Privacy policies, manuals, and documentation
This pillar ensures that compliance is provable. Regulators expect accurate, up-to-date policies and manuals that reflect real processing activities, guide employees, and support audits, investigations, and regulatory inquiries. -
Data breach response and incident management
This pillar prepares organizations to respond effectively when incidents occur. It covers breach identification, notification timelines, response roles, documentation, and post-incident review to meet legal obligations and limit regulatory exposure.
Regulators do not look at these pillars in isolation. A gap in any one area can weaken the entire compliance posture, even if other controls are well established. What matters most is how well governance, risk management, documentation, and incident response work together to show that privacy compliance is active and consistently applied, not just written on paper.
Pillar 1: Data Protection Officer appointment and accountability
This pillar establishes who owns privacy decisions and how that responsibility is enforced across the organization. Regulators assess whether privacy accountability is real, visible, and embedded into governance, not merely documented.
When a Data Protection Officer is required
The NPC requires a DPO appointment when processing activities create a material risk to data subjects. In practice, this applies in the following scenarios:
-
Large-scale personal data processing: Organizations that process significant volumes of customer, employee, or citizen data on a continuous basis are expected to designate a DPO due to the heightened impact of errors or misuse.
-
Handling sensitive personal information: Processing health, financial, biometric, or government-issued data triggers stricter accountability expectations because of the potential harm to individuals.
-
Use of monitoring, profiling, or analytics technologies: Systems that track behavior, analyze individuals, or automate decisions increase risk and therefore require formal DPO oversight.
Key responsibilities of the Data Protection Officer
Regulators expect the DPO to actively influence decisions, not simply provide advice when asked. Core responsibilities include:
-
Oversight of the privacy management program: The DPO ensures policies, risk assessments, and controls are implemented consistently and aligned with regulatory requirements.
-
Advisory role in business and technology decisions: Leadership and operational teams rely on the DPO to flag privacy risks tied to new systems, vendors, data sharing, or analytics use cases.
-
Primary regulatory and data subject contact: During audits, complaints, or breach investigations, the DPO represents the organization and coordinates responses with the authority.
Registering and maintaining DPO accountability
Formal accountability must be visible to regulators and consistently maintained. Organizations are expected to demonstrate:
-
Timely and accurate NPC registration: DPO details must be registered within prescribed timelines and reflect the actual individual performing the role.
-
Ongoing accuracy of registration information: Changes in role, contact details, or organizational structure must be promptly updated to avoid compliance gaps.
-
Operational involvement of the registered DPO: Regulators assess whether the registered DPO is reachable, informed, and actively engaged in governance activities.
Pillar 2: Privacy impact assessment and risk management
PIAs address a common compliance failure: launching initiatives before understanding data risk. Regulators rely on PIAs to confirm that risks are assessed, mitigated, and documented before processing begins.
When to Conduct a Privacy Impact Assessment
PIAs are expected whenever processing may significantly affect data subjects. Common trigger points include:
-
Processing of sensitive or regulated data types: Health, financial, biometric, or government-issued data requires advanced risk assessment due to higher potential harm.
-
High-volume or centralized data processing: Large databases and shared analytics platforms increase exposure and, therefore, require documented risk evaluation.
-
Introduction of new systems or external processors: Cloud migrations, AI tools, vendors, or cross-border processing must be assessed before data is transferred or activated.
Core steps in a Privacy Impact Assessment
A defensible PIA follows a structured process that regulators expect to see applied consistently.
-
Mapping the processing activity: This includes identifying data sources, purposes, data subjects, storage locations, and access points across systems.
-
Assessing risk to data subjects: Risks such as unauthorized access, excessive collection, misuse, or prolonged retention are evaluated by likelihood and impact.
-
Defining and documenting mitigation measures: Technical, organizational, or contractual controls are recorded along with approvals to support audit readiness.
Why PIAs matter beyond compliance
When used properly, PIAs strengthen governance and decision-making across teams.
-
Preventing non-compliant processing early: Risks are addressed before systems go live, reducing remediation costs and regulatory exposure.
-
Providing defensible audit evidence: Documented PIAs demonstrate due diligence during investigations, complaints, or breach assessments.
-
Supporting privacy-by-design practices: Risk assessment becomes part of planning rather than an afterthought.
Pillar 3: Privacy management program and governance structure
This pillar ensures privacy compliance is systematic rather than ad hoc. Regulators expect a formal program that distributes accountability across functions.
Elements of an effective Privacy Management Program
An effective program provides structure and continuity through:
-
A documented governance framework: Oversight roles, escalation paths, and decision authority are clearly defined and consistently applied.
-
Policies, procedures, and standards: Legal requirements are translated into repeatable operational practices.
-
Monitoring and periodic reviews: Compliance posture is reviewed as systems, vendors, and data use evolve.
Defining privacy roles and responsibilities
Regulators assess whether accountability extends beyond the DPO.
-
Cross-functional ownership: Legal, IT, HR, security, and business teams have documented responsibilities tied to data handling.
-
Clear escalation and decision authority: Privacy issues can be raised and resolved without ambiguity during incidents or audits.
-
Management-level accountability: Senior leadership reinforces that privacy obligations are mandatory, not discretionary.
Embedding privacy into business operations
Sustainable compliance requires integration into daily workflows.
-
Privacy checks within operational processes: Procurement, system development, vendor onboarding, and analytics include built-in privacy review steps.
-
Alignment with real-world practices: Controls reflect how teams actually work, reducing workarounds and policy drift.
-
Support for growth without friction: Privacy-by-design is applied without slowing execution or innovation.
Pillar 4: Privacy policies, manuals, and documentation
Privacy compliance often breaks down not because controls are missing, but because documentation does not reflect how data is actually processed. Regulators assess written policies as evidence of intent, accountability, and operational maturity.
It is a core pillar that demonstrates how privacy obligations are translated into everyday practice and enforced across the organization.
Required privacy policies and manuals
Before reviewing controls, regulators assess whether documentation exists and is appropriate.
-
External privacy policies: These explain lawful processing, rights, retention, and safeguards in language that data subjects can understand.
-
Internal privacy manuals: Employees receive clear guidance on handling personal data access across systems and roles.
-
Incident and breach response documentation: Procedures align with notification timelines and reporting obligations.
Keeping policies aligned with legal requirements
Policies lose value when they are generic or outdated.
-
Operational translation of legal obligations: Legal requirements are converted into clear, actionable steps.
-
Consistency with actual systems and workflows: Policy commitments match how data is processed in practice.
-
Regular updates based on change: Documents evolve with regulatory guidance, systems, and data use.
Maintaining accurate and up-to-date documentation
Audit readiness depends on documentation discipline.
-
Clear ownership and approval responsibility: Each document has an accountable owner and review authority.
-
Version control and change history: Updates are tracked to show how compliance evolves over time.
-
Centralized and accessible records: Evidence can be produced quickly during audits or investigations.
Pillar 5: Data breach response and incident management
Data breaches are one of the most visible indicators of privacy compliance failure. Regulators do not assess organizations only on whether breaches occur, but on how quickly, accurately, and responsibly they are identified, escalated, and reported. This pillar focuses on preparedness, decision-making, and documentation during incidents, not just technical containment.
Identifying a notifiable data breach
Not every incident is automatically reportable, which is why regulators examine how organizations assess impact and risk. A breach becomes notifiable when it poses real harm to data subjects.
-
Unauthorized access, disclosure, or loss of personal data: Incidents involving hacking, misdirected emails, lost devices, or system compromise must be evaluated for exposure and impact.
-
Risk-based assessment of harm: Organizations are expected to assess whether the breach could result in financial loss, identity theft, discrimination, or reputational damage.
-
Gray-area incidents requiring judgment: Even partial exposure or temporary access may still require notification if risk to individuals cannot be ruled out.
Breach notification timelines and obligations
Once a breach is deemed notifiable, timing and completeness become critical. Regulators focus heavily on whether notifications meet legal expectations.
-
72-hour notification to the National Privacy Commission: The NPC expects notification within the prescribed window after discovery, not after full investigation concludes.
-
Notification to affected data subjects: Individuals must be informed when the breach is likely to pose a real risk, using clear and non-technical language.
-
Completeness and accuracy of reporting: Notifications must include facts, impact assessment, mitigation steps, and contact details, not vague or incomplete disclosures.
Responding to and documenting incidents
Beyond notification, regulators assess whether incidents are handled in a controlled and accountable manner.
-
Defined incident response roles and escalation paths: Teams must know who leads containment, communication, and regulatory coordination during a breach.
-
Structured response and containment actions: Technical, operational, and organizational steps should be coordinated to limit further exposure and preserve evidence.
-
Post-incident documentation and review: Root cause analysis, corrective actions, and lessons learned must be documented to prevent recurrence.
|
Stat: According to IBM Security, the global average cost of a data breach reached $4.45 million, with higher costs linked to delayed response, weak governance, and poor documentation. |
How to operationalize the five pillars at scale
Defining the five pillars is only the first step. The real challenge begins when organizations try to apply them consistently across teams, systems, and growing data volumes. Regulators increasingly assess whether privacy compliance is operationalized, embedded into day-to-day workflows, rather than managed through isolated documents or individuals.
Limitations of manual compliance processes
Many organizations start with manual methods, but these approaches break down quickly as complexity increases. Over time, they introduce risk rather than control.
-
Fragmented tracking across spreadsheets and emails: Privacy obligations such as DPO tasks, PIAs, policy updates, and breach logs are often tracked in separate files, making oversight inconsistent and error-prone.
-
High dependency on individual knowledge: Compliance continuity suffers when key personnel leave or roles change, as institutional knowledge is rarely centralized or documented properly.
-
Increased risk of missed obligations: Manual processes struggle to keep up with timelines for reviews, registrations, and breach notifications, leading to gaps that regulators frequently flag.
Using tools and automation to support privacy programs
As data environments scale, automation becomes essential for maintaining consistency and audit readiness. Regulators do not mandate tools, but they expect outcomes that manual methods rarely sustain.
-
Centralized visibility into compliance posture: Tools help consolidate PIAs, DPO records, policies, and incident logs into a single system, making oversight clearer and more defensible.
-
Real-time alerts and evidence collection: Automated reminders, risk triggers, and documentation logs reduce reliance on memory and ensure actions are traceable during audits.
-
Reduced operational burden on privacy teams: By streamlining repetitive tasks, automation allows DPOs and compliance teams to focus on governance and decision-making rather than administration.
Conclusion
Building a sustainable data privacy program requires more than policies and periodic reviews. The five pillars only work when accountability, risk assessment, documentation, and incident response are connected and consistently enforced across systems.
As data environments grow more complex, many organizations struggle to maintain this alignment using manual processes and disconnected tools.
This is where OvalEdge adds value. By delivering centralized visibility into data assets, lineage, ownership, and policy context, OvalEdge helps organizations operationalize privacy compliance at scale.
Teams gain the ability to identify personal and sensitive data, support Privacy Impact Assessments, maintain audit-ready documentation, and respond to incidents with confidence and control.
If your privacy program feels fragmented or difficult to scale, it may be time to strengthen how these pillars work together in practice.
Book a Demo with OvalEdge to see how privacy compliance can move from a reactive effort to a governed, operational capability that supports long-term growth.
FAQs
1. Is the five-pillars data privacy framework mandatory in the Philippines?
The law does not name the five pillars explicitly, but regulatory requirements under the Philippines Data Privacy Act effectively enforce them through DPO registration, PIAs, documentation, breach reporting, and accountability standards assessed during audits.
2. Who is responsible for enforcing data privacy compliance inside an organization?
Enforcement does not rest solely with the DPO. Ultimate accountability lies with senior management, while operational enforcement spans legal, IT, HR, and business teams based on documented governance and decision ownership.
3. Can small or mid-sized companies follow the five pillars of data privacy compliance?
Yes. Smaller organizations can scale the pillars proportionally by simplifying documentation, limiting high-risk processing, and prioritizing essential controls, as long as accountability, risk assessment, and breach readiness remain demonstrable.
4. How often should organizations review their data privacy compliance framework?
Organizations should formally review their privacy framework at least annually, and immediately after system changes, new data uses, vendor onboarding, or regulatory updates that affect personal or sensitive data processing.
5. What happens if an organization fails to comply with the five pillars?
Non-compliance can result in regulatory investigations, fines, processing restrictions, reputational damage, and criminal liability for responsible officers under the Philippines Data Privacy Act, depending on severity and negligence.
6. Are automation tools required to implement the five pillars effectively?
Automation is not legally required, but it significantly improves consistency, monitoring, and audit readiness, especially for organizations handling large data volumes or operating across multiple systems and regulatory jurisdictions.
Deep-dive whitepapers on modern data governance and agentic analytics
OvalEdge recognized as a leader in data governance solutions
.png?width=1081&height=173&name=Forrester%201%20(1).png)
“Reference customers have repeatedly mentioned the great customer service they receive along with the support for their custom requirements, facilitating time to value. OvalEdge fits well with organizations prioritizing business user empowerment within their data governance strategy.”
.png?width=1081&height=241&name=KC%20-%20Logo%201%20(1).png)
“Reference customers have repeatedly mentioned the great customer service they receive along with the support for their custom requirements, facilitating time to value. OvalEdge fits well with organizations prioritizing business user empowerment within their data governance strategy.”
Gartner, Magic Quadrant for Data and Analytics Governance Platforms, January 2025
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
GARTNER and MAGIC QUADRANT are registered trademarks of Gartner, Inc. and/or its affiliates in the U.S. and internationally and are used herein with permission. All rights reserved.


.png)
